Information Security Risk Management
Information Security Risk Management
Our company has established an “Information Security Risk Management Procedure” to regularly assess risks and ensure the implementation of risk mitigation measures. We evaluate risks annually to effectively identify and control various risks faced by the company. We also implement risk management, handling, and subsequent improvement measures to reduce risks to an acceptable level and ensure uninterrupted business operations.
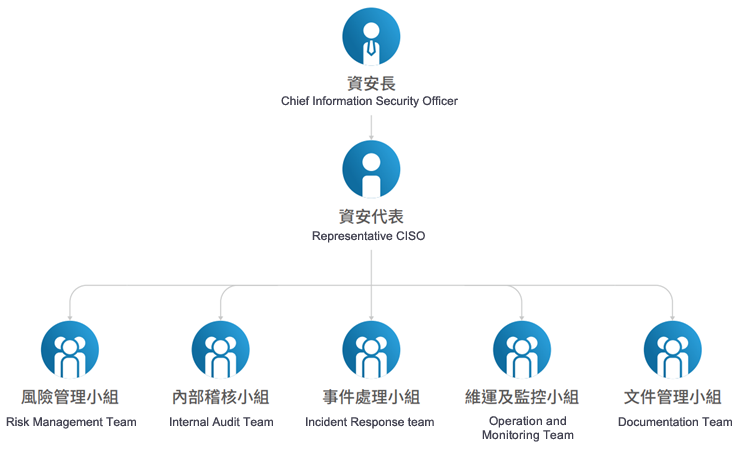
Information Security Steering Committee Organization Structure
In 2016, the Information Security Steering Committee was established to maintain the normal operation of the information security management system.
In 2020, the dedicated information security management organization – Information Security Department was established to provide specialized functions to lead, coordinate, and advise on network security issues, activities, and threat intelligence. This is to proactively detect, investigate, and respond to the network security threats faced by Wisdom Corp.
Information Security Policy
1. All personnel (including regular employees or outsourced personnel, such as on-site vendors, part-time staff, and consultants, etc.) are responsible and obligated to protect the relevant information assets of their assigned business areas to ensure the confidentiality, integrity, and availability of important information assets of the Group.
2. The job responsibilities of employees should be appropriately segregated, and only necessary permissions and information required to perform their duties should be granted.
3. Personnel recruitment should undergo necessary assessments and sign relevant operational regulations, and participate in information security education and training to understand the obligation of each individual to maintain and protect information security, which should be implemented in daily work.
4. Establish a mechanism for the continuous operation of business operations and regularly test drills to maintain their applicability.
5. The information security measures of the Group should comply with legal requirements and the requirements of the Group’s information security policy. The establishment and modification of all information security regulations or procedures must comply with and follow the mechanism of the information security management system.

